Cyberterrorism as a political act and the actions it implies on European organisations.
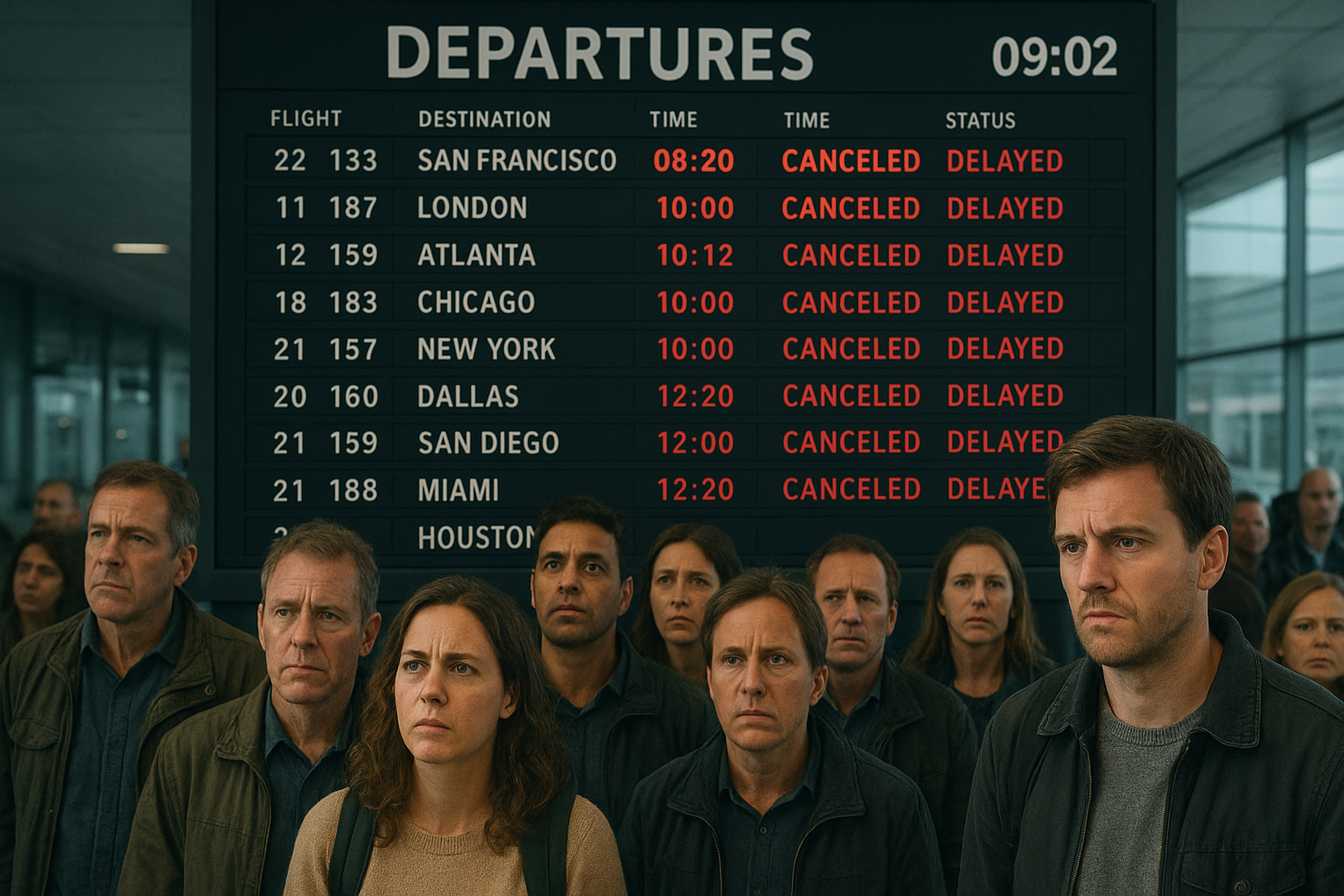
Saturday September 20th the world woke up to news that several European airports amongst which hubs like London Heathrow, Berlin Brandenburg and Brussels Airport. These airports had serious operational problems checking customers in for flights, causing long delays and even canceled flights. The cause was quickly found to be a cybersecurity incident at a supplier of software, to be more precise, a Software as a Service (SaaS) application called MUSE, from a company called Collins Aerospace.
After some time, it became clear that it was in fact a Ransomware attack, and specifically had been targeting the ARINC system which is responsible for collecting passengers biometric data. An official attribution has not yet been made, although ENISA did say they have identified the type of malware used.
The timing however is interesting. Only 24 hours before the ransomware was activated, Collins Aerospace and its mother RTX (formerly known as Raytheon) announced they had won a large NATO contract. This of course can be a coincidence, but most people working in the cyber security field know that coincidence is the least likely option.
Considering the fact that the NATO is in a de facto skirmish with Russia through Ukraine, makes it more than likely that Russia is somehow involved in this attack. Likely, access to the systems of Colins Aerospace was already established a while back, and the timing of the attack was triggered by the announcement of winning a NATO contract. Aim? Basically to show the West that they are vulnerable.
This is the new reality. Geopolitical events can trigger attacks with the aim to cause fear and uncertainty for both governments as well as mere consumers. This time it was a system used in airports. What if next time it is a water distribution system? Or traffic lights software supplier? Or electricity network operator?
This is why Cybersecurity and -preparedness is essential for any organization in the EU active in the essential sector, as defined in the last year adopted NIS2 directive. Assume you are breached and have sleeping network access to an Advanced Persistent Threat actor. Assume they can, at the click of a button, disrupt systems that impact your core processes. What are you going to do?
Resilience is essential. Ensure you have offline backups of all your data. Have a playbook how to act in such a case. Not just from an IT perspective, but also on managerial level and communications, both internal as well as external. To media, customers, your government and shareholders. Ensure you have ways to restore operations, and a plan B if IT systems are not as easy to bring back up as hoped (again, assume they are not). And train people for these events, because the whole world will be watching when it happens.